Entry 2 - Unit 5 - Using ICT: Safe Working Practices
Handbook home page
Activities supporting the assessment of this award
Assessor's guide to interpreting the criteria
General Information
-
The Bronze 2 Award is designed to provide progression from the Entry Level 1 Bronze award to Entry level 3 Award and as a foundation for Level 1 ICT user qualifications particularly the ITQ.
-
The definition of an entry level qualification is to recognise basic knowledge and skills and the ability to apply learning in everyday situations under direct guidance or supervision. Learning at this level involves building basic knowledge and skills and is not geared towards specific occupations.
-
The criteria are designed to provide opportunities to promote numeracy, literacy and social skills as well as ICT capability and are fully compatible with the UK National Curriculum programmes of study.
-
The Bronze 2 Award is designed to promote a wider range of participation by providing coherent progression from the Bronze 1 to Bronze 3 and/or Silver Level 1 qualifications. We want especially to include people with special needs or specific learning difficulties and younger children. Contexts for learning should be chosen appropriately for the learner.
-
The specification for the Bronze 2, Entry Level 2 Award provides an outcome framework for assessment and is not intended to dictate any particular context for learning and so can be used with young children or adults. The INGOTs family of qualifications are designed for personalising learning rather than targeting arbitrary groups. Assessors have discretion about the contexts used as long as the assessment criteria can be matched and the guidance below should be read with this in mind.
Requirements
-
Standards must be confirmed by a trained Bronze Assessor or higher
-
Assessors must at a minimum record assessment judgements as entries in the on-line mark book on the INGOTs.org certification site.
-
It is expected that there will be routine evidence of work used for judging assessment outcomes in the candidates' records of their day to day work. Samples should be available at the annual visit and/or by video conference.
-
Different approaches to learning will be required in order to match differing needs, for example, the needs of children will be different from the needs of adults with learning disabilities.
-
Completing the criteria entitles the candidate to the Bronze 2 Award. In general, the candidate should demonstrate that matching criteria can be sustained over time with continued practice.
-
We expect at least 15 hours of guided study to be under-taken before the award is made assuming learners are new to computers but discretion can be used to take account of prior learning where this is sensible in individual cases. In terms of making the award, what matters is outcomes and competence.
Assessment Method
Assessors can use the criteria to determine levels of prior learning through dialog with the candidate, direct observation and any other appropriate and relevant evidence. They can score each of the criteria for each candidate N (No evidence), L (some progress but still lower than the level) S, secure at that level and this criterion, H, the candidate is performing beyond the required level. Candidates are required to achieve S or H on all the criteria to achieve the full award. This means they provide evidence of "Secure" competence across all the criteria.
Expansion of the assessment criteria
- the task or context will be familiar and involve few factors (desktop computer, laptop, mobile phone, opening a document, selecting an object, naming keyboard, mouse, screen); and
- the techniques used will be familiar or commonly undertaken with support from other more experienced people.
Learners should show willingness to be co-operative and respect the advice and support given by more experienced users.
1. The learner will know about health and safety measures that should be followed when using ICT equipment
1.1 I can outline safety checks that need to be made prior to using ICT equipment
- there is sufficient space to work in a comfortable position, with opportunities for varying movements and posture.
- lighting arrangements should be satisfactory and ensure an appropriate contrast between the display screen and the background environment. Glare and reflections (e.g. from windows or sunlights) should be avoided, with blinds (preferably vertical) used to prevent sunlight falling on display screens. Surfaces should have a matt finish to avoid glare and reflections.
- noise levels created by workstation equipment should not be distracting to the user/operator.
- no item of workstation equipment should generate excess heat that could cause user/operator discomfort.
1.2 I can state how often breaks should be taken when using a computer
1.3 I can state a reason for taking breaks when using a computer
1.4 I can demonstrate personal posture needed when using a desk top computer
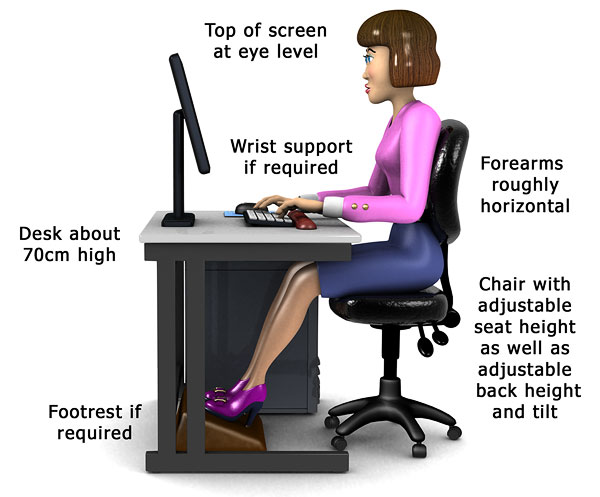
1.5 I can state where support can be obtained when adjustments are required for own safety and comfort
2. The learner will know about PINs and passwords
2.1 I can give examples of where PINs and passwords may be required
2.2 I can state why PINs and passwords need to be secure
2.3 I can state how to keep PINs and passwords secure
Moderation/verification
The assessor should keep a record of assessment judgements made for each candidate and make notes of any significant issues for any candidate. They must be prepared to enter into dialog with their Account Manager and provide their assessment records to the Account Manager through the on-line mark book. They should be prepared to provide evidence as a basis for their judgements should it be required by the Principal Assessor or their Account Manager/external moderator. Before authorizing certification, the Account Manager must be satisfied that the assessors judgements are sound.
